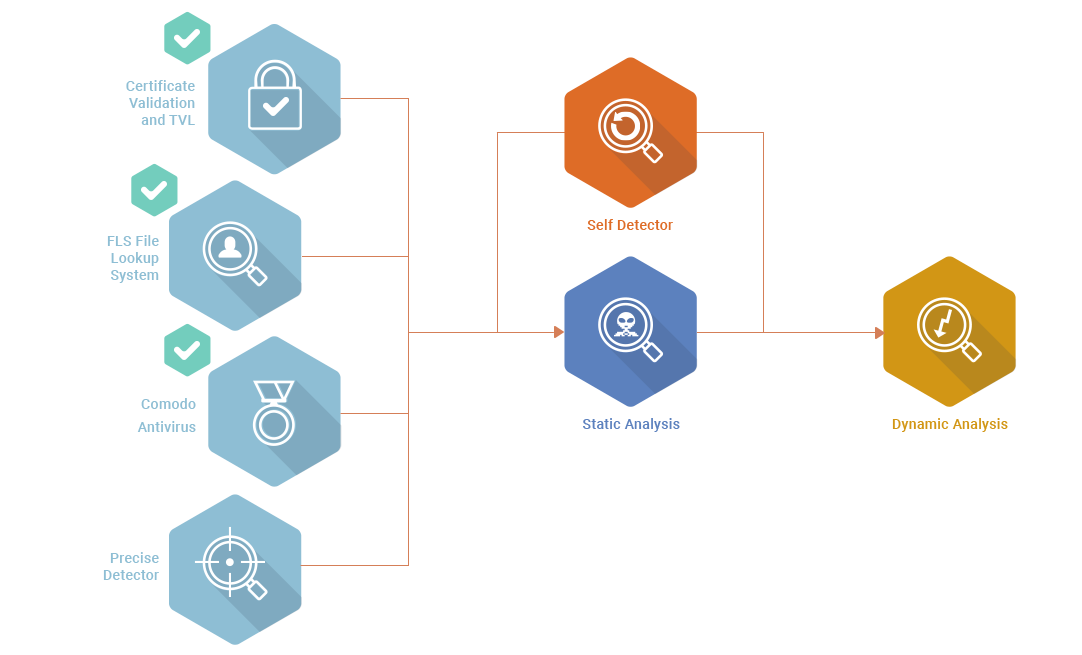
How we detect at the endpoint
Comodo takes a holistic approach to endpoint security that spans simple signature-based detection of known malware to application whitelisting to advanced detection and response tools at the local level and in the cloud. Comodo’s endpoint security continuum also includes application and network access controls, a host intrusion prevention firewall (HIPS) and patent-pending Secure Auto Containment™ for usability while preventing infection from unknown malware.
For more information please visit project’s website from here The manuals and sample sets are at the Here is What You Get section.